NexusTek Recognized Among Elite 150 in 2019 CRN MSP 500 List for Third Year in a Row

- February 19, 2019
NexusTek Recognized Among Elite 150 in 2019 CRN MSP 500 List for Third Year in a Row
Enhanced cloud services portfolio, nationwide expansion, culture and commitment to customer experience cement company’s position among upper echelon of managed IT services leaders
Denver, CO (February 19, 2019) – NexusTek, a leading national provider of cloud, cyber security and managed IT services, today announced that for the third year in a row CRN®, a brand of The Channel Company, has named NexusTek to its 2019 Managed Service Provider (MSP) 500 list in the Elite 150 category.
“We are honored to have been named an Elite 150 managed services provider by CRN for the third consecutive year,” said NexusTek CEO, Mike Jenner. “This distinction reflects a company-wide commitment to delivering a better customer experience by empowering small to medium-sized businesses with the latest technology solutions and hi-touch support to power their success.”
This annual list recognizes North American solution providers with innovative approaches to managed services.
Managed service providers are integral to the success of businesses everywhere. They empower companies to implement and operate complex technologies while staying within their budgets and keeping focus on their core business. CRN’s MSP 500 list identifies the most groundbreaking managed service organizations, with advanced solutions that have endless potential for growth.
NexusTek achieved record growth in 2018. Today, thousands of businesses across the country trust NexusTek to manage and optimize their respective IT environments for business continuity, productivity and costeffectiveness. Leveraging highly skilled people, enterprise class processes and industry leading technology, NexusTek presents the SMB marketplace with a single partner to offer true end-to-end IT managed services.
NexusTek provides the convenience and assurance of working with one partner that has the breadth of technology, track record, engineers and dedicated support teams to design, deliver, on-board and maintain IT operations, whether in the public cloud, hybrid, on-premise or multi-cloud environments.
“Fast-growing companies competing in today’s innovation economy must be agile,” added Jenner, “and cannot risk being held back by technology they’ve outgrown. NexusTek is not limited by geography or technology. We have the nationwide resources to scale with customers as they grow in size and footprint, and to address their needs – both present day and future.”
Despite the numerous potential benefits of cloud, cyber security and managed IT services, only the right solutions – and partner – can solve security, business and auditing requirements. NexusTek, an SSAE 16 SOC II certified company, proves its adherence to rigorous, industry-accepted auditing standards for service companies year after year. Important to note, is that as of 2018, NexusTek has also qualified for the GDPR rider.
“Capable MSPs enable companies to take their cloud computing to the next level, streamline spending, effectively allocate limited resources and navigate the vast field of available technologies,” said Bob Skelley, CEO of The Channel Company. “The companies on CRN’s 2019 MSP 500 list stand out for their innovative services, excellence in adapting to customers’ changing needs and demonstrated ability to help businesses get the most out of their IT investments.”
The MSP500 list will be featured in the February 2019 issue of CRN and online at www.CRN.com/msp500
Share On Social
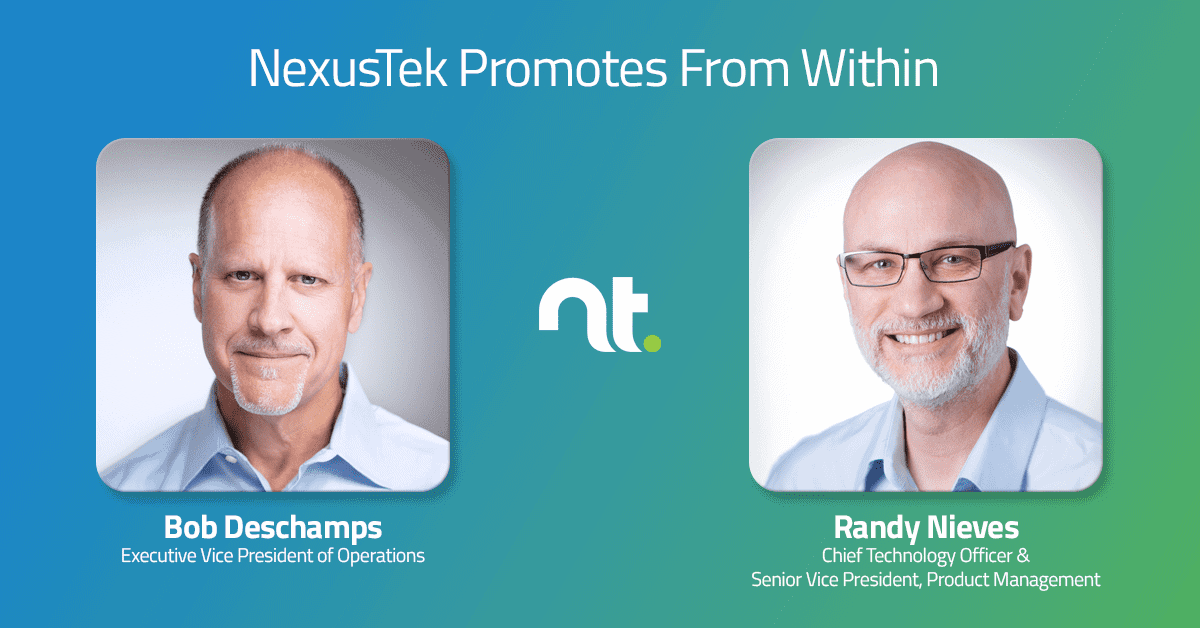
NexusTek Elevates Bob Deschamps to Executive Vice President of Operations and Randy Nieves to Chief Technology Officer and Senior Vice President of Product Management

- February 13, 2019
NexusTek Elevates Bob Deschamps to Executive Vice President of Operations and Randy Nieves to Chief Technology Officer and Senior Vice President of Product Management
Award winning managed IT services leader promotes from within to strengthen Executive Leadership Team
Denver, CO (February 13, 2019) NexusTek, a leading provider of cloud, cyber security and managed IT services, announced today that it has promoted two of its most tenured senior leaders: Bob Deschamps to Executive Vice President (EVP) of Operations and Randy Nieves to Chief Technology Officer (CTO) and Senior Vice President (SVP) of Product Management .
“In addition to the veritable treasure trove of knowledge and IT services expertise accrued over decades, Randy Nieves and Bob Deschamps know this company from top to bottom,” said Mike Jenner, CEO, NexusTek, “and NexusTek takes pride in being able to promote from within. An intimate familiarity is not only one of the many intangibles both Bob and Randy bring to our Executive Leadership Team, but also a core element in NexusTek’s ability to deliver better services to businesses nationwide.”
As EVP of Operations, Deschamps directs NexusTek’s cloud and premise-based services delivery force, comprised of more than 200 engineers, technicians and client service representatives.
“For businesses that want to leverage cloud services but don’t have the in-house personnel to manage a migration, NexusTek Cloud Services extend the flexibility and control businesses need to be agile, and can address customers’ unique cyber security, business continuity, compliance and auditing requirements in public cloud, managed private cloud, hybrid, multi-cloud or on-premise environments,” said Bob Deschamps. “Many services are built with a one-size-fits-all mentality and leave little room for customization. Conversely, NexusTek Cloud Services offer a scalable, resilient and flexible environment that can meet the needs of organizations of all sizes – and in all markets.”
Deschamps carries more than 30 years of top-tier management experience in operations, sales and finance for globally-recognized brands including General Motors, Arrow Electronics and Microsoft.
As CTO and SVP for Product Management, Nieves is now tasked with developing, enhancing and deploying NexusTek products, services and solutions, as well as charting the company’s strategic roadmap for technology, enablement and training. In directing product lifecycle management process from end to end, Nieves and his team collaborate closely with partners to create innovative, disruptive and profitable offerings tailored for current and future market conditions.
“I am thrilled to join the NexusTek Executive Leadership team and to be entrusted with architecting the roadmap for the reigning MSP of the Year,” said Randy Nieves. “Over the past several years, this company has forged ahead while other service providers have faded away due to their inability to scale and retain talent. For businesses that want the competitive advantage of working with a single partner that can not only manage, but optimize their IT environments, NexusTek provides nationwide infrastructure, IT consulting expertise and an all-encompassing portfolio to solve today’s problems and tomorrow’s needs.”
Nieves brings more than 28 years of leadership experience and a broad base of engineering, design, operational, consulting, and logistics knowledge to his new post. Throughout his almost three-decade career, Nieves has excelled in building and leading IT consulting and Network Operation Centers (NOC). In addition, he has exceptional engineering experience across a wide array of technology and operating systems including private, public and hybrid cloud environments, network and storage infrastructure, virtualization, wireless communications, firewalls, disaster recovery services, security, and point of sale systems. Nieves also holds several technical certifications including CSSA, CSSP and ITIL v3, as well as extensive experience ensuring compliance for industry regulations such as PCI, HIPAA, GDPR and ITAR.
With an all-encompassing services portfolio, national infrastructure and workforce, NexusTek offers end-to-end IT management that sets a new standard in how businesses consume managed IT services. Tenured executives like Randy Nieves and Bob Deschamps provide the expertise and leadership with which NexusTek helps customers improve business outcomes.
Share On Social
WOWSA – Customers Benefit From a Great Corporate Culture
READ TIME: 2 MIN

- January 30, 2019
WOWSA – Customers Benefit From a Great Corporate Culture
In the IT world, we are often measured by how quickly and efficiently we can solve problems. We are experts with machines, virtuosos of virtualization and magicians with code. Our goal is zero downtime and staying connected is critical to our success. Yet, despite being connected nearly 24×7, IT industry employees are part of the nation’s statistics that show only 33% of employees are engaged at work. Like people in all industries, IT professionals need personal connection, meaning, and purpose. At NexusTek, we are determined to far exceed that statistic.
Through our WOWSA employee engagement program, we strive to help our employees find contentment and purpose in the workplace. WOWSA stands for “Why Our Workplace Stays Awesome” and we work hard to make that a reality. Our team’s passion and energy create amazing results for our customers.
To wrap up 2018, we surveyed all of our 300+ NexusTekers around the country and asked them to identify which values they identified with the most. Then, we held a series of internal focus groups to discuss what our organization’s core values and mission statement should be moving forward.
We are proud to share the values the NexusTek family has chosen:
- Our Mission: Enabling the latest technology solutions for small to medium-sized businesses to power their success.
- People: We value our team members and have a passion for what we do.
- Community: We are united for the good of our Company and the business communities we serve.
- Courage: We adapt and reach above and beyond.
- Integrity: We act ethically, honestly, and fairly.
- Performance: We deliver what we promise.
Since forming the WOWSA employee program many years ago, the committee has evolved to an inspiring level. Today, we coordinate many volunteering events and serve many nonprofit organizations through “WOWSA Gives,” our corporate giving program, along with implementing employee programs. Knowing that our team has volunteered to help so many individuals brings our employees a sense of fulfillment and pride. The true spirit of the program is to engage with our incredible network, serve our communities in a meaningful way and build personal connections.
Creating a place where our employees thrive, result in an extraordinary customer experience delivered by the most talented, dedicated engineers in the industry. Nurturing a culture-driven company isn’t easy, and in today’s world where companies face constant pressure to profit, finding that balance is difficult.
We are proud to say that NexusTek is making great strides to rise to the top with strong business growth and a leading corporate culture.
What’s on the Horizon for Cloud Computing?
READ TIME: 2 MIN

- January 30, 2019
What’s on the Horizon for Cloud Computing?
As cloud technology for small to medium-sized businesses continues to advance, a multi-cloud strategy is becoming the choice for growth-minded companies. This strategy is not without its challenges and some business owners may doubt the ease of managing one data migration and platform let alone multiple instances. The trend in cloud services for business is leveraging the power of a multi-cloud architecture for that competitive advantage in your market.
Defining Multi-Cloud Architecture
The term ‘multi-cloud’ refers to organizations using multiple cloud offerings (usually from different cloud providers) to manage their data. While a hybrid cloud refers specifically to supplementing on-site storage with an off-site cloud, multi-cloud architecture can stand on its own, or serve as part of a larger hybrid infrastructure.
Choosing the Right Vendor
When choosing the right cloud vendor for your business, make sure you have a clear understanding of the technology used. How reliable is the uptime? What’s the failover rate? Are there redundant data centers in case of a local power outage? A combination of private and public cloud instances allows companies to reap the benefits without compromising functionality.
The three most important aspects of functionality are computing, backup, and disaster recovery. This strategy isn’t vendor specific and will allow flexibility with hosted applications. For example, you can link cloud components with application components without restrictions if you later decide to switch providers.
Best Practice with Vendors
Regularly backing up your data in an easily consumable format will reduce the likelihood of future issues, whether accidental or malicious. As well, having security and disaster recovery options are crucial to maintaining business continuity and could mean the difference between being back online in under an hour, or business failure.
Emerging tech trends is another aspect you’ll want to consider when exploring a multi-cloud architecture. Reconfiguring your applications to run on a new platform, is both costly and time consuming. Using open platforms, on the other hand, allows organizations to isolate software and have them running on top of their infrastructure. When it comes time to transition to a new cloud provider – as technologies become more cost effective – those applications are easy to relaunch.
Cloud Providers on the Horizon
Today, there are many cloud providers to choose from and the trend on the horizon suggests even more will enter this growing market. The increase in competitors is sure to drive opportunities for you and your business.
At NexusTek, we can help match the right cloud provider to your mission-critical systems, allowing you to mature your operations while seeing a great return on your investment in IT.
Share On Social
Protecting Your Assets with a Solid Cyber Security Strategy
READ TIME: 2 MIN

- January 30, 2019
Protecting Your Assets with a Solid Cyber Security Strategy
When considering a cyber security strategy, think in terms of creating concentric rings around your most important assets. Your first task is to determine your most important assets and then categorize them in terms of risk.
Here are some examples of information assets you may want to include:
- Employee HR information
- Health benefits information
- Social security numbers
- Business financial documents
- Customer lists
- Customer confidential information
- Much more…
Your ability to protect employee and customer information is bound by many regulations and records compliance. A breach compromising these assets not only would damage your brand reputation but could lead to legal battles, loss of business or complete business failure.
The idea of concentric rings as a cyber security strategy is very simple; guard your assets against accidental loss or destruction, nefarious actions by outsiders or even someone within your organization.
Backup, Threat Protection and Monitoring
A good backup protocol can eliminate accidental loss or destruction of your most critical data. Having a strong high-availability and disaster recovery process can guard against downtime.
Next, implementing data loss prevention(DLP) is a good way to make sure your highest risk (your employees) are not ex-filtrating data from your business. DLP can provide your organization with policies on access controls for viewing, editing, printing, downloading, and emailing various documents and files. Therefore, you are implementing total control over your proprietary information.
Create another ring of security in the form of threat protection for your email and endpoints. This is a great way to add on a meaningful layer or security, enabling you to catch anomalous activity before it wreaks havoc in your environment.
Implement a full-environment monitoring service to add that final ring. This is protection from the edge, all the way to your internal systems allowing for full visibility of all activity from all sources, whether activity slips through endpoint protection by an employee social media activity, a click on a malicious link, or loading up a compromised thumb drive, your monitoring service is watching 24x7x365 to make sure you’re protected.
Remember, there is no silver bullet to cyber security. The best you can do is to protect your company on many different layers and be diligent about your employees adhering to a policy of protections.
Stay safe out there! – Lynn Shourds, Vice President of Sales at NexusTek
Share On Social
3 Things to Know When Updating Your Phone System
READ TIME: 3 MIN

- January 30, 2019
3 Things to Know When Updating Your Phone System
Lower Your Cost of Ownership
Modern communications have certainly evolved well beyond the vision of our forefathers. When we reflect on the number of touchpoints we now manage between employees and customers, it is no wonder the pace of business growth is at an all-time high. Whether it’s email, chat, messaging apps, or video conferences, you need open communication to run your business. So, as you’re comparing phone systems and unified communications platforms, here are some things you’ll want to consider.
Right Plan, Right Person
When calculating the cost of a new phone system, you’ll want to factor in “add ons” to get the features and capabilities that will best serve your business goals. One of the advantages of working with NexusTek is our ability to tailor your Unified Communications System to your business needs, so each employee has the service level they need based on their daily workflow. If you require that your management team has access to deeper analytics and monitoring capabilities, but you only need basic functionality for the rest of your staff or call center, you can lower your total cost of ownership by picking the right plan for each person.
Minimizing Business Risk
Most business owners agree that risk is a scary word. You might take risks on marketing a new product but when it comes to your phone system, taking risks is like driving without insurance. By partnering with NexusTek, we’ll help you reduce your risk by controlling all communications on our platform end-to-end. Your customers’ data stays secure while you stay compliant – making it a “win-win” for your business and your customer!
Grow the Right Way
Growth can be another scary proposition for business owners. From big decision like moving into new markets, opening new offices, or acquiring new businesses, ensuring that your operational standards are maintained across your organization is a requirement.
Let NexusTek worry about setting up your communications system and adhering to regulatory environments. At the end of the day, our service is more than just phone coverage. NexusTek can help you comply with local telecommunications rules, set up your offices with local numbers and provide an interface that your employees’ can feel comfortable with using from the start.
When choosing a Unified Communications partner, it’s critical to dive into the technology, business relationships, and support capabilities of each provider you consider. NexusTek listens to your own specific communications needs to ensure your new phone system exceeds your expectations. Contact us about NexusTek’s Unified Communications program to learn more.
Share On Social
Could You Do More to Prevent Cyber Attacks?
READ TIME: 2 MIN

- January 30, 2019
Could You Do More to Prevent Cyber Attacks?
Let’s face it, just about every organization could do more to thwart the cyber threats in today’s digital age. If you’re not sure where to start, we’ve got the best tool for you.
NexusTek’s FREE Cyber Security Self-Assessment can help you stay ahead of cybercrime by identifying vulnerabilities before you get hit.
As 2018’s Microsoft Partner of the Year for Project Management & Modern Workplace, NexusTek has been given a unique opportunity to offer your business this Cyber Security Self-Assessment. This quick survey covers more than 20 security points in four key cyber security categories. The purpose of this self-assessment is to pinpoint your cyber security strengths and weaknesses, and provide a complete Cyber Security Health Check Report containing useful tips and recommendations in the following cyber security categories.
- Prevent/Identify a Compromise – Help prevent against a compromise within your environment while uncovering potential breaches
- Secure Apps and Data – Boost productivity with cloud access while keeping your information protected
- Expand Device Controls – Deliver enhanced security across both company and personal devices
- Safeguard your Infrastructure – Enforce policies that help keep cloud resources and hybrid environments safe
The self-assessment takes 5-10 minutes to complete. Once you submit your completed assessment, you will receive a custom report containing your cyber security scores and an expert’s recommendations covering security check points across identity, apps and data, devices and infrastructure. In addition, you will have the opportunity to schedule a FREE Cyber Security Consultation with one of NexusTek’s security experts. Start 2019 off right by ensuring your business is protected against cyber attacks.
Take your self-assessment here: https://partnersiteprd.wpengine.com/Cybersecurity-Self-Assessment
Share On Social
Collection No. 1 – Has Anyone Not Been Pwned?
READ TIME: 4 MIN

- January 28, 2019
Collection No. 1 – Has Anyone Not Been Pwned?
There are approximately 7 billion humans on Planet Earth. Recently, over ten percent of them – 773 million of them, to be exact – now have their sensitive personal information released into public record. This is courtesy of what’s known as Collection No. 1, one of the largest collections of unique email addresses and passwords ever to be released.
Importantly, Collection No. 1 is not the result of a single data breach. Rather, it is a farrago – multiple separate and previously unheard-of data breaches accumulated into a single mass and released for public consumption.
Data breaches at this scale are illustrative. Not only do they show us how many people constantly reuse weak and insecure passwords across the internet, they also show us something about how data – emails, passwords, phone numbers, and so on – are used once it has been stolen. Here’s what the Collection No. 1 breach tells us about information security.
How to Use Stolen Data
Most stolen data isn’t immediately useable. Even if a hacker successfully steals a list of email, username, and password combinations, they’ll usually find that the password is protected by something called a hash. A hash is a one-way cryptographic algorithm that renders passwords into a protected format. Most applications never store plain-text passwords – only the hash is stored. When you put your password into a login form, it gets hashed and then checked against the stored hash for verification.
Hashes are not unbreakable, and hackers are creative. If you have a weak password, hackers can find it through something called a rainbow table attack or a dictionary attack, in which they take an example list of weak passwords, hash them, and then check a stolen database for matching hashes.
Alternatively, hackers may find that they’ve stolen a list from a company that does not adhere to good password management practices. For example, they might be using depreciated hashes – hashes that are widely solved and easy to decrypt. A lot of companies still use the MD5 hash, even though it’s been known to be insecure since 2005.
Even though there are methods, de-hashing stolen data takes a ton of work – which is what makes the Collection No. 1 breach so notable. Each one of the millions of passwords that were released as part of Collection No. 1 have been de-hashed. That means that they are immediately available for hackers to use – and most likely, they’ve already tried to use them.
The Lifecycle of Stolen Data
Data that’s stolen from companies and organizations doesn’t often get used right away. For example, criminals that steal data directly often don’t have any interest in or ability to de-hash it. That means that this data gets immediately sold. The buyer will then attempt to de-hash this data, and it takes time – stubborn hashes can take months or even years to decrypt.
Once the hashes have been decrypted, the hackers will attempt to use the resulting credentials – they’ll try to unlock bank accounts and steal money, or potentially use admin credentials to break into corporate networks and steal more information. Not all credentials will be easy to use – they might not be closely associated with either companies or bank accounts – and not all of them will still be valid by the time they’ve been decrypted.
Huge data dumps like Collection No. 1 are the end result of this process. This is the data that has either already been mined for immediate usefulness or can’t easily be mined for immediate profit. The only thing that’s left for attackers to do is use it for what’s known as credential-stuffing attacks: taking huge lists of various usernames and passwords and then running them through various services in the hope of finding a useful combination.
Expect to see a lot of credential-stuffing attacks using the data from Collection No. 1 (and subsequent collections) in the coming weeks and months.
Protect Your Business with Help from NexusTek
Data breaches like Collection No. 1 highlight the need for companies to create secure password management strategies and protect their businesses from account hijacking. NexusTek can help with both. Our security experts will consult with companies in order to develop password protection schemes that use state-of-the-art cryptographic algorithms to protect user data. In addition, we offer monitoring solutions that can detect and mitigate the influx of login attempts that would accompany a credential stuffing attack.
Information security hinges on protecting user data and mitigating intrusion attempts – and NexusTek specializes in both. For more information on how to work with us, contact NexusTek today.
Share On Social
The Security Risks of Employee Online Shopping
READ TIME: 3 MIN

- January 23, 2019
The Security Risks of Employee Online Shopping
The holiday season has come and gone. While I’m sure you hoped your employees closed out the year on a high note, the reality is that they were probably a bit preoccupied with all the shopping they had to do. Throughout December 2018, analysts expected $65.5 billion worth of online transactions.
In a perfect world, you’d expect your employees to keep all of this online shopping to their personal time (outside of the office). However, more than half of employees say they’ll spend work hours shopping online during the holiday season. Amazon validated this assertion when, on the day after Christmas, it announced that 2018 was a record-breaking holiday season for the eCommerce giant.
And that’s only the holiday season. Easy access to online shopping exists year-round and as such, is a never-ending security risk for your business.
Be honest – you didn’t love every single gift you received. According to research from WalletHub, 34 percent of Americans plan to return a gift this year. For business owners, this shows the need for constant diligence to defend against cyber attacks.
While it’s important to limit risky employee behavior, the best way to secure your business is to maintain real-time visibility of your network.
Social Engineering and the Risks of Online Shopping at Work
Even if you have strict policies to block non-work-related websites on your office network, employees still find ways to visit social media profiles and eCommerce sites.
But the security risks don’t come from eCommerce sites exclusively. Sites like Amazon, Walmart, and other popular eCommerce websites won’t inject malware into your network just from employees shopping on them.
The real security risks lie in social engineering threats. Attackers know that the majority of data breaches are caused by human error. One carefully-crafted email can lure employees into opening malware-laden attachments or clicking malicious links that compromise your network.
These kinds of threats are tied directly to online shopping in the workplace. When employees shop online through your network, they’ll often log into their personal email accounts to access coupons and special deals.
One misclick as they sift through large volumes of personal emails can release a virus, ransomware, or other type of foothold in your business network. According to Rob Otten and Michael Allen at Security InfoWatch:
“Unlike corporate email, which often blocks suspicious links and attachments, personal email cannot be easily filtered for malicious content by the enterprise. Webmail content is typically delivered over end-to-end encrypted communications, such as HTTPS, allowing attachments received via personal accounts to completely bypass the organization’s content filters.”
One of the best ways to combat these online shopping threats in the workplace is to create a culture of security. When you’re continuously training employees and building awareness of potential phishing threats, you can harden the front lines of your business network without any new technology.
But awareness training can only get you so far. You can’t eliminate human error and employees will keep finding ways to shop online during work hours. To fill the gaps, you need total network visibility and real-time monitoring.
Keep Your Network Secure 24/7/365
Whether you’re up against increased online shopping for the holiday season or you need to curb the ongoing vulnerabilities throughout the year, you can’t take a set-it-and-forget-it approach to security. Simply deploying a firewall and anti-virus software won’t get the job done.
To shore up vulnerabilities related to human error, online shopping, and other risky employee behaviors, you need:
• Real-Time Monitoring: Attackers can spend days or even weeks within your network if you don’t have the proper monitoring tools and practices. Any amount of disruption can have costly repercussions, so you need real-time insights into traffic anomalies and potential threats.
• Security Operations Center (SOC): Your network is constantly evolving, and it takes a full-time team to analyze the organization’s security posture. With a SOC, you have a dedicated set of security pros who are ready to plug any holes in your network security.
• Penetration Testing and Vulnerability Assessment: Network security is no longer just about reacting to threats. You have to proactively address vulnerabilities and spot weak points that attackers could target.
These are just a few of the keys to network security that can offset the risks of employee online shopping. But for many businesses, it’s too costly and complicated to bring them all in-house.
If you want a managed security provider that can partner with you for all your network protection needs, contact us today and find out how we can help.